How can Check Point Infinity help your organisation?
In today’s ever evolving cyber security landscape, securing your organisation against threats is imperative. As the world advances and moves further into cyber space with everything connected all of the time, we must ensure our security moves just as quickly to keep up with any new threats that may appear. That is why we are excited to share this blog, written by our CEO, Paul Starr, on why Check Point Infinity offers a consolidated cyber security architecture which can help secure your organisation.
Check Point Infinity Architecture and Enterprise License Agreement is well documented by Check Point and therefore some of the information in this post is taken from Check Point directly. However, in this blog post, we want to bring attention to some key features of Check Point Infinity and how it can help your organisation.
Protecting against cyber threats has become more complex than ever, with the world more connected and our business and personal lives being always online, we are seeing more advance persistent threats (APTs) occur, using techniques to hide in the shadows and blend in with legitimate traffic, collecting information before striking.
Additionally, our world is rapidly changing with new technologies and services promising simplification, efficiencies, and cost saving. we onboard these new services & technologies faster than we have ever done. We often evaluate these in isolation and look to single point solutions to protect and reduce risk, which is ineffective and can be costly.
Therefore, with ever-increasing numbers of threat actors and sophisticated cyber-attacks occurring across our endless points of connection to the internet and increasing threat vector, it is more important than ever to remember that ‘we are only as strong as our weakest link’. We must demand the highest level of protection across endpoint, mobile, cloud and our ‘traditional’ networks.
This is where Check Point Infinity comes in. Check Point have long been leaders and well known in Firewall Security, however, in recent years Check Point has built a portfolio which includes Network, Endpoint, Mobile, Email & Office and Cloud security. Check Point are no longer just Firewalls.
This has led to the Check Point Infinity Architecture which enables organisations to prevent cyber threats, simplify security management, and boost efficiency.
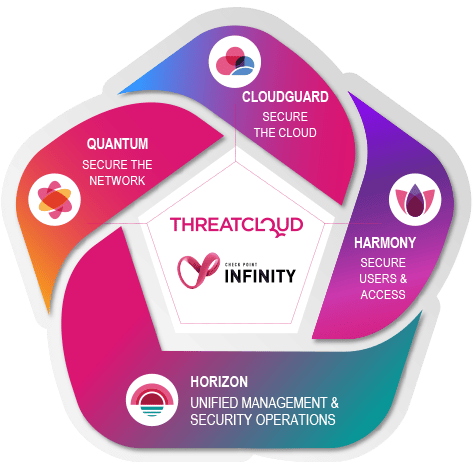
“Check Point Infinity is a fully consolidated cyber security architecture which protects your organisation and IT infrastructure against cyber–attacks across all networks, endpoint, cloud and mobile, sharing threat intelligence across all security environments.” Check Point Website
Check Point have strived to build the best individual products, but the overarching mission is to build a unified security architecture to make business more secure and security operations more efficient & effective.
Shared Threat Intelligence
Powered by Check Point ThreatCloud, the world’s largest cyber threat intelligence database, handling 86 billion transactions daily. Gathering and correlating data from more than 100,000 Check Point customers with Check Point researchers enriching the ThreatCloud with intelligence about the latest attacks.
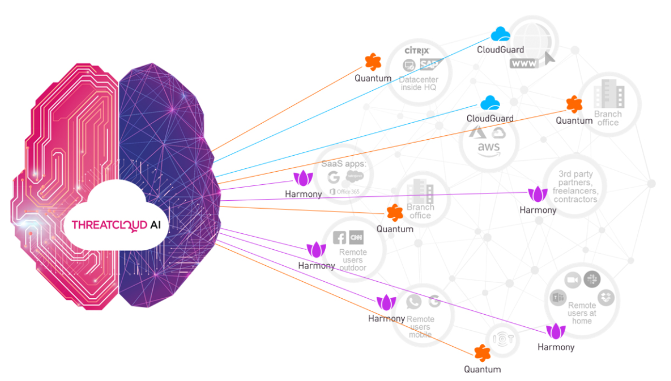
ThreatCloud leverages artificial intelligence to anticipate unknown attacks and uncover new vulnerabilities, constantly analysing big data to automatically identify threats. This intelligence is shared across the entire Check Point solution range, covering networks, endpoint, cloud and mobile.
If a malicious email is sent to O365 inbox and blocked via Harmony Email & Office; Threat cloud receives the IOC, expands to additional IOCs resulting in:
- An SMS message with malicious link blocked Harmony Mobile
- Another user(s) browsing to an infected site is blocked via the Quantum Gateway or Harmony Connect or Harmony Endpoint.
- A cloud server is infected, and its C&C communication is blocked at Quantum Gateway or Harmony Endpoint.
Providing the organisation with the same protections across all environments, without sacrificing security.
Check Point focus on protection before detection & Check Point Zero Trust
Check Point has always prided themselves on promoting a protection-first strategy, identifying that detection was no longer enough. This philosophy has been implemented across the entire portfolio to make sure their customers get the best security and is complimented with Check Point Zero Trust.
Security professionals are shifting to a Zero Trust Security state-of-mind: no device, user, workload or system should be trusted by default, neither inside or outside the security perimeter, and with the large adoption of remote/hybrid working the inside/outside perimeter is even harder to define. Designing or rebuilding your security infrastructure around a Zero Trust approach using point solutions might lead to complex deployment and inherent security gaps.
Check Point offers a practical and holistic approach to implement Zero Trust, based on single consolidated cyber security architecture, Check Point Infinity (https://www.checkpoint.com/solutions/zero-trust-security/).
- Zero Trust Networks – Zero Trust security is about having the ability to segregate and secure your network to reduce the risk of lateral movement. Harmony Connect Remote Access takes secures access to any internal enterprise network or application residing in the data centre, IaaS, public or private clouds. Where the Security Gateways enable you to create granular network segmentation across public/private cloud and LAN environments.
- Zero Trust People – With a large proportion of data breaches involving stolen credentials, username and passwords do no longer prove the identity of a user. Identities are easily compromised. Check Point Identity Awareness ensures access to your data is granted only to authorized users, and only after their identities have been strictly authenticated, using Single Sign-On, Multi-Factor Authentication, context-aware policies. Harmony Connect Remote access offers least privileged access for diverse users, including internal and external identities, by integrating into directories, identity providers and offering PAM-as-a-service for engineers, administrators, and DevOps.
- Zero Trust Devices – Security teams must be able to isolate, secure, and always control every device on the network. Check Point solutions enable you to block infected devices from accessing corporate data and assets, including employees’ mobile devices and workstations, IoT devices and Industrial Control Systems. In addition, Check Point Advanced Threat Prevention for Endpoints always protect employees’ devices and maintain your corporate security policy on untrusted networks.
- Zero Trust Workloads – Securing workloads, particularly those who are running in the public cloud, is essential since these cloud assets (e.g. containers, functions, and VM’s) are vulnerable, and attractive target to malicious actors. Check Point Infinity includes cloud security solutions that integrate with any public or private cloud infrastructure and provide full visibility and control over these ever-changing environments.
- Zero Trust Data – Zero Trust is all about protecting the data while it is shared continuously between workstations, mobile devices, application servers, databases, SaaS applications, and across the corporate and public networks. Check Point Infinity delivers multi-layered data protection, that pre-emptively protects data from theft, corruption, and unintentional loss, wherever it is.
- Visibility & Analytics – You can’t protect what you can’t see or understand. A Zero Trust Security model constantly monitors, logs, correlates, and analyses every activity across your network. Check Point Infinity is managed via Centralised Security Management which provides security teams full visibility into their entire security posture.
- Automation & Orchestration – Zero Trust infrastructure should support automated integration with the organization’s broader IT environment to enable speed and agility, improved incident response, policy accuracy, and task delegations.
Check Point Infinity Licencing
While there is a huge security benefit to Infinity, there is also a simplified licencing operation benefit to get the full threat prevention your enterprise needs in a simple all-inclusive, per-user, per-year, subscription offering. Infinity Enterprise License Agreement is a security business model that enables you to consume all the products and solutions included within the Check Point Infinity security architecture, along with all the associated services you need.
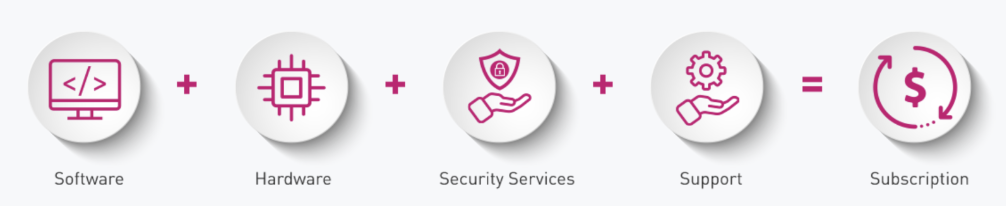
Tailor made solutions across industries, verticals and company sizes, Infinity Enterprise Licence Agreement enables you to consume the security products and associated services you need.
Get in touch with SEP2 today to find out how Check Point Infinity can help your organisation stay secure.








